Keeping you in the know
Whatever you're interested in, get engrossed in our latest research, insights and blogs. We’ll put the kettle on, you have a browse.
Whatever you're interested in, get engrossed in our latest research, insights and blogs. We’ll put the kettle on, you have a browse.

30 min read
Our 2025 Email Security Trends report reveals insights from 400+ IT leaders and 2000 employees across the UK, USA, and Europe to uncover predictions, opinions, and insights into the state of email security.

20 min read
Learn how to prove the ROI of your solutions. Industry experts Simon Newman, Co-Founder of Cyber London, and Frank Horenburg, Head of IT at Zivver, share insights and expertise on identifying and sharing the value of security.
12 min read
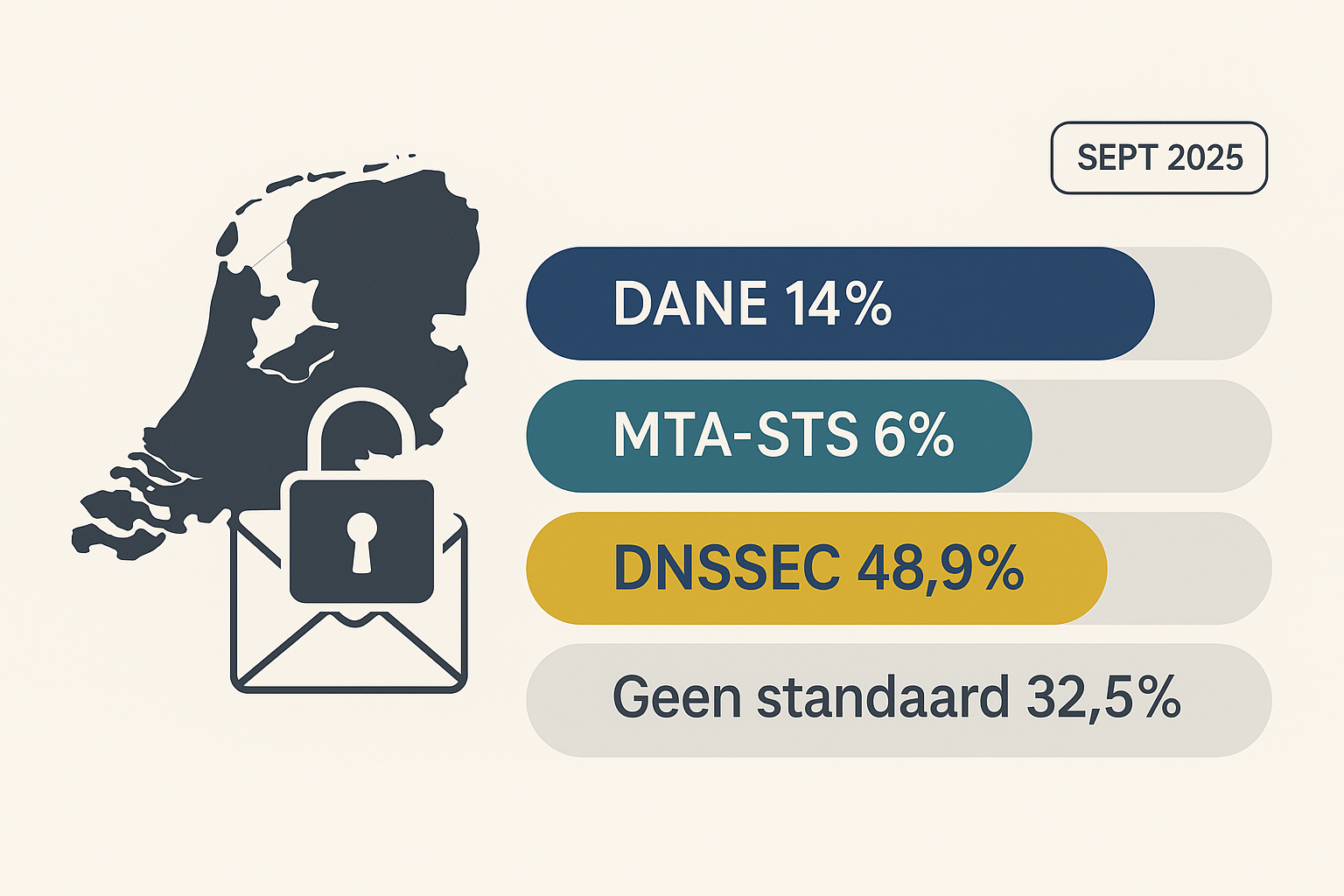
Summary Only 14% of the domains analyzed support DANE, and just 6% support MTA-STS. This means that over 80% of domains still fail to meet the basic standard for secure email transport. One in three d...

23 min read
Email remains the most widely used digital communication channel in organizations, but it was never designed as a secure medium. The risks of unsecured email are significant: interception, human error...

1 min read
We’re thrilled to share that Zivver has been shortlisted for the Bridging the Privacy and Security Gap Award at the PICCASO Awards 2025, marking our fourth consecutive appearance on the shortlist.

Learn how email data loss prevention keeps sensitive information safe.

30 min read
Our 2025 Email Security Trends report reveals insights from 400+ IT leaders and 2000 employees across the UK, USA, and Europe to uncover predictions, opinions, and insights into the state of email security.

Understand your encryption options for secure business comms

Hear insights from AI and cybersecurity leaders on how to build cyber resilience through AI powered tools and training.

Learn actionable insights on how security leaders can take action to enhance their organizaton’s cyber resilience

Hear insights from cybersecurity leaders on how to prevent data leaks and improve security awareness.

4 min read
Combination delivers on commitment to uncompromising data privacy and security to European organizations Amsterdam, Netherlands – June 18, 2025 – Zivver, Europe’s leading provider of secure communicat...
2 min read
May 2025: Zivver is proud to announce its inclusion in the 2025 DataTech50 list by FinTech Global, recognising the company as one of the most innovative technology providers driving transformation in ...
2 min read
Zivver founders Dr. Rick Goud and Wouter Klinkhamer celebrate 10 years since launch of Zivver
Subscribe to get more email security tips straight to your inbox.